- NIST released FIPS 203, 204, and 205: New post-quantum cryptography standards designed to protect against emerging quantum threats
- The standards cover key encapsulation mechanisms (ML-KEM), securing shared private information, and validating digital signatures (ML-DSA and SLH-DSA), addressing various aspects of cryptographic security
- TQ42 Cryptography provides a NIST-validated, comprehensive solution, offering both open-source and commercial options for organizations transitioning to post-quantum security
Quantum computers have the potential to break the cryptographic algorithms that protect our digital world today, leaving sensitive data vulnerable. In response, the National Institute of Standards and Technology (NIST) has been working on new cryptographic standards designed to protect against these emerging threats. In particular, NIST has released FIPS 203, FIPS 204, and FIPS 205 – three post-quantum cryptography standards that pave the way for a more secure future. In this blog, we will explain the need for post-quantum cryptography and provide an overview of the new standards.
Cryptographic Keys
A cryptographic key is represented in a computer as a string of bits. In symmetric cryptography, a shared secret key is jointly computed by two parties such that it is identical for both of them and is kept secret from adversaries. Asymmetric cryptography, on the other hand, uses two different keys: a public key for encryption (or encapsulation) and a private key for decryption (or decapsulation).
The Quantum Threat
Quantum computing introduces new computational methods that can attack widely used cryptographic algorithms. The two algorithms of note are Grover’s algorithm, which could target symmetric cryptography, and Shor’s algorithm, which targets asymmetric cryptography. Let us take each in turn.
Grover’s algorithm was developed in 1996. It provides a quadratic speedup in brute-force attacks against popular forms of symmetric cryptography, such as AES. This speedup only slightly weakens their security levels. For example, AES-256 being targeted by a quantum computer would have the same security as AES-128 being attacked by an ordinary computer. Consequently, the most pragmatic response to this threat is to continue to employ AES but with larger key sizes.
Shor’s algorithm was developed in 1994. It efficiently solves the mathematical problems underlying the most common forms of asymmetric cryptography, RSA and ECC, rendering them breakable by a sufficiently powerful quantum computer. The threat of Shor’s algorithm is so significant that the world needs to migrate its asymmetric cryptography to new post-quantum methods that are based on completely different mathematical problems. The publication of FIPS 203, 204, and 205 is an important early milestone in this migration.
Overview of NIST’s New Standards
FIPS 203 – Module-Lattice-Based Key-Encapsulation Mechanism Standard
FIPS 203 specifies ML-KEM, a key encapsulation mechanism that allows two parties to securely establish a shared secret key over a public channel. The shared secret key can then be used with symmetric encryption algorithms to secure communication, ensuring confidentiality and authenticity.
FIPS 204 – Module-Lattice-Based Digital Signature Standard
FIPS 204 specifies ML-DSA, a set of algorithms that can be used to generate and verify digital signatures. It can be used to detect unauthorized modifications to data and to authenticate the identity of the signatory. It is intended for use in email, electronic funds transfers, electronic data interchanges, software distribution, data storage, and other applications that require data integrity assurance and data origin authentication.
FIPS 205 – Stateless Hash-Based Digital Signature Standard
FIPS 205 defines SLH-DSA, a method for digital signature generation, verification, and validation. Its security relies on the difficulty of finding preimages for hash functions as well as several of their related properties. It can be used to authenticate the integrity of signed data and the identity of the signatory. Recipients of signed messages can use the digital signature to demonstrate to a third party that the signature was, in fact, generated by the claimed signatory. In other words, the signatory cannot easily deny or repudiate the signature at a later time.
Implementation Timelines and Readiness
NIST released these standards on August 13, 2024, marking a crucial step in post-quantum cryptography adoption. While no mandatory implementation date has been set, NIST is 'encouraging computer system administrators to begin transitioning to the new standards as soon as possible' [NIST News, August 2024].
On the day of this milestone, U.S. National Cyber Director Coker emphasized the urgency of this transition in his White House remarks, stating, "The threat isn't just on the horizon; it's here now.", highlighting the "store-now, break-later" risk. He noted that the U.S. government has been inventorying systems for vulnerable cryptography, prioritizing high-value assets for the cryptographic transition. This underscores the importance for organizations, especially those in regulated sectors or working with government agencies, to begin assessing their systems and planning integration of these standards immediately.
An infographic presenting the Department of Homeland Security's Post-Quantum Cryptography Roadmap offering guidance for organizations planning this transition, indicates their expectation of a cryptographically relevant quantum computer to be “potentially available” by 2030.
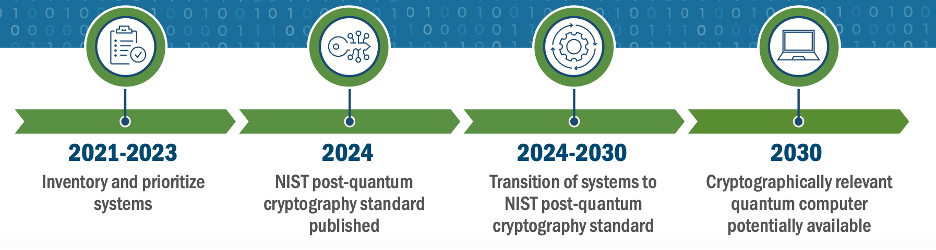
Source: U.S. Department of Homeland Security - Preparing for Post-Quantum Cryptography: Infographic
Organizations, especially those in regulated sectors or working with government agencies, should begin assessing their systems and planning integration of these standards. Early adoption ensures readiness for future requirements and demonstrates commitment to robust security against evolving threats.
Employing NIST-Validated Cryptography
The Solution
As announced in a previous blog post, Terra Quantum’s implementation of the latest NIST-standardized algorithms (FIPS 203, FIPS 204, FIPS 205) has successfully passed the NIST Cryptographic Algorithm Validation Program (CAVP). This NIST-aligned post-quantum cryptography library from Terra Quantum has both open-source and commercial licenses.
Diving deeper into this, NIST maintains a list of validated cryptographic algorithm implementations, which is crucial for organizations seeking compliant solutions. Terra Quantum's TQ42 Cryptography has successfully passed NIST's Cryptographic Algorithm Validation Program (CAVP) across various operating environments, demonstrating our commitment to meeting the highest standards of security and compliance. Our NIST validation ensures that organizations using TQ42 Cryptography can confidently meet regulatory requirements and industry best practices. This validation sets us apart as a trusted provider of post-quantum cryptographic solutions, ready to support organizations in their transition to quantum-resistant security.
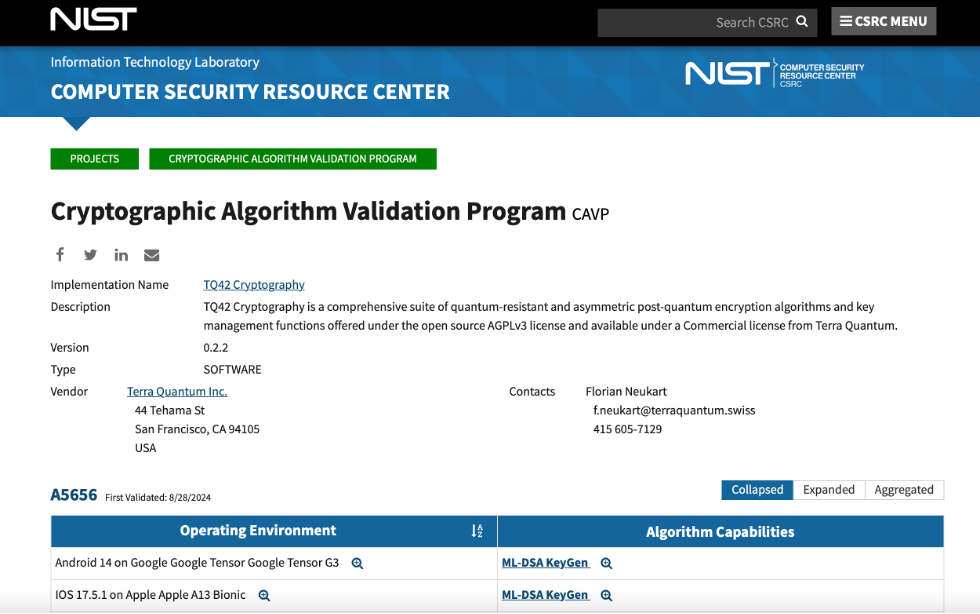
Source: NIST
TQ42 Cryptography not only implements these standards but also offers a comprehensive suite of post-quantum algorithms. Our library provides a seamless path for organizations to transition their cryptographic systems to quantum-resistant alternatives, ensuring long-term data security and regulatory compliance.
What Sets TQ42 Cryptography Apart
TQ42 Cryptography stands out as one of the most comprehensive, NIST-aligned post-quantum cryptography solutions, for several reasons:
- Comprehensive Features: Our library implements all three NIST-standardized PQC algorithms (FIPS 203, 204, and 205), along with a complete suite of quantum-resistant cryptographic tools, security features and incorporated randomness source.
- Robust Testing: TQ42 Cryptography has been rigorously tested across multiple operating environments, ensuring reliability and performance across diverse systems.
- Flexibility: Available in both open-source and commercial versions, TQ42 Cryptography caters to a wide range of organizational needs and preferences.
- Future-Ready Design: Our modular architecture supports emerging algorithm standards and quantum enhancements, allowing for seamless updates as the field evolves.
- Performance Optimized: TQ42 Cryptography is designed for efficiency, minimizing the performance impact often associated with post-quantum algorithms.
- Easy Integration: We provide comprehensive documentation and support to facilitate smooth integration into existing systems, reducing the complexity of transitioning to post-quantum security.
- Backed by Quantum Expertise:As part of Terra Quantum's broader suite of quantum technologies, TQ42 Cryptography benefits from our deep expertise in quantum computing and its security implications.
By choosing TQ42 Cryptography, organizations not only gain a NIST-validated post-quantum cryptography solution but also partner with a leader in quantum technology, ensuring they stay ahead of emerging quantum threats and opportunities.
When and How to Employ
At the time of writing, the foreseeable future consists not only of government regulations but also of support. The regulations will be focused on the industries where both the chances and the costs of data breaches are highest. As we have seen with NIST’s CAVP, the support will come from government programs through which suitable cryptographers with expertise in post-quantum cryptography can become accredited. These accredited cryptographers can then operate as consultants and assist organizations in their planning and roll-out of post-quantum cryptography.
When and How to Prepare
The migration to post-quantum cryptography will occur at different times for different sectors of the economy. Preparation is needed so that organizations who should be first movers don’t suddenly become urgent adopters.
Initially, the preparation should consist of accurately conveying the quantum threat to an organization’s risk managers, decision-makers or stakeholders. First movers should be aware that state-of-the-art quantum computers are no longer in the “noisy intermediate-scale quantum” era, where noise prevents large-scale implementations of quantum algorithms. Recently, they have moved into the “fault-tolerant” era, where it is possible to effectively suppress noise. Carefully assessing and then presenting the associated risks still requires some scientific literacy. For sectors of strategic importance, waiting until the quantum threat is a clear and obvious risk is not an option.
A very practical aspect of an organization’s preparation is to look for commonalities with other cybersecurity initiatives, whether these are adopting a more crypto-agile cybersecurity posture or moving to a zero-trust security model. Many such initiatives begin by conducting a cryptographic inventory and migrating to post-quantum cryptography is no different. Consequently, updating one’s cybersecurity practices in a comprehensive manner that involves the consideration of post-quantum algorithms can have significant benefits over a more piecemeal approach.
Take the Next Step
The release of FIPS 203, 204, and 205 marks a critical point, akin to hitting the reset button in post-quantum cryptographic security. Organizations that act now to implement these standards will be well-positioned to protect their data against advanced current and future threats. With TQ42 Cryptography, you can rely on a reliable, NIST-validated, comprehensive solution.
Whether you're a developer exploring open-source options or an enterprise seeking a commercial-grade solution, TQ42 Cryptography offers a secure and compliant path forward in the quantum era. Ready to quantum-proof your systems with a validated, future-ready solution? Contact our team to start planning your post-quantum cryptography migration roadmap.
Stay tuned for our next blog post in the series, where we'll dive deeper into the details of FIPS 203.