Quantum Security
The world's current encryption systems are vulnerable, and the threat of hackers trying to 'store now, decrypt later' poses huge challenges for entities entrusted with data. We provide ubiquitous quantum security through our growing suite of comprehensive solutions.
Your Path to Quantum-Secure Readiness
We simplify your transition to quantum security with a guided journey—starting from awareness, moving through risk assessment, and ending in decisive action.

Your Guided Path to Quantum Security
Move from awareness to action with confidence. Our structured journey helps you understand quantum threats, assess your risk, and implement quantum-safe solutions with clarity and purpose.
Assessment: Audit, Choose & Plan
Getting started can be intimidating; we help you understand where you are, where you want to go, and how to get there.
Assessing Quantum Security Readiness
- Cryptographic Analysis: Analyze all assets and determine their cryptographic protection. Lean on established frameworks such as NIST's Cyber Security Frameworks and the Cyber Defense Matrix.
- Maturity & Readiness: Map the maturity & readiness of the state-of-the-art technology being used in the systems and applications you want to make quantum-secure (your "target systems").
- Critical Vulnerabilities: Identify the critical vulnerabilities and threat actors to determine the timeline to make the target system quantum-safe.
- Action Plan: Identify the critical vulnerabilities and threat actors to determine the timeline to make the target system quantum-safe.
3 Key Pieces of Quantum Security Puzzle
Quantum security relies on solving hard problems, generating true random keys, and distributing them securely.
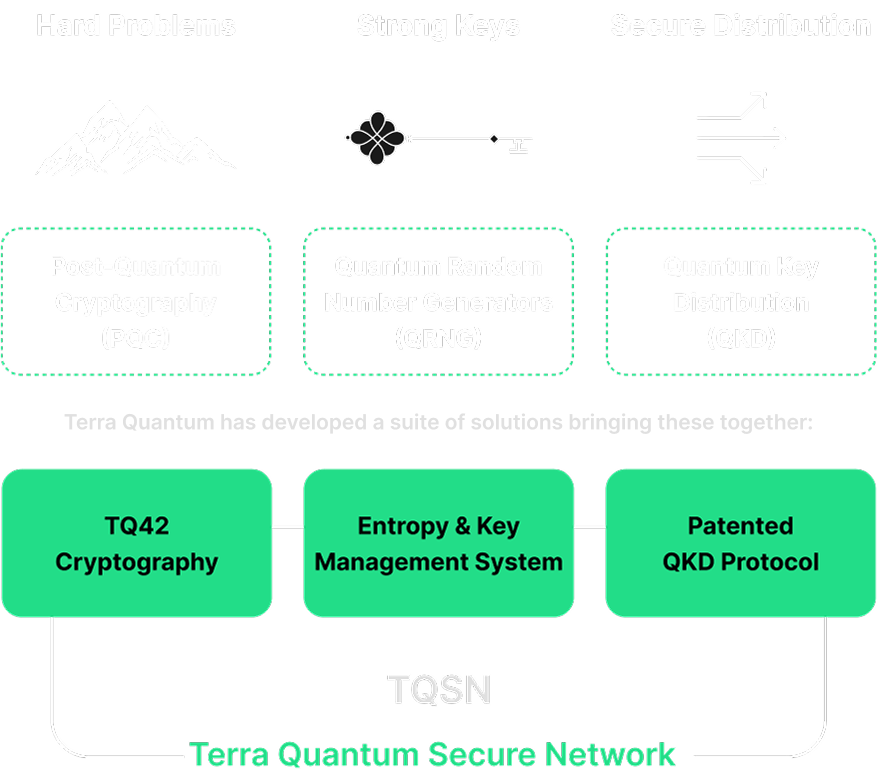
Our Quantum Security Suite Offerings
Quantum-secure solutions for encryption, key generation, and distribution.
TQ42 Cryptography, our NIST-aligned and validated PQC library, features cutting-edge post-quantum algorithms for secure data transmission, storage and authentication, offering protection against advanced quantum threats.
Our QRNG service utilizes the inherent unpredictability of quantum phenomena to produce genuinely random cryptographic keys, providing an unassailable foundation for your quantum security infrastructure.
TQSN, powered by our patented QKD protocol, distributes keys with unconditional security, making key interception mathematically impossible and ensuring the integrity of your communications.
We're Aligned with the Standards
We implement post-quantum standards from compliance and standards bodies and enhance them with proprietary solutions in QKD, QRNG and PQC. We've submitted to – and passed – NIST-compliant test suites for our QRNG hardware and PQC software.
Quantum-Ready Cryptography for Modern Security
TQ42 is a NIST-aligned open-source library offering validated post-quantum cryptography to help secure your applications against current and future threats.
TQ42 Cryptography with NIST-Aligned and Validated PQC Algorithms
Our open-source post-quantum cryptography library, aligned with NIST standards and validated through CAVP, is designed to help businesses protect their data from current and future security threats. This cutting-edge suite of post-quantum algorithms and key management functions complements our existing offerings, providing an accessible entry point for organizations to integrate quantum-resistant security measures into their applications.
Key Library Features
A robust suite of cryptographic tools for secure communication, encryption, and key lifecycle management.

SHA-3(224, 256, 384, 512, SHAKE -128,SHAKE-256)

Enabled by Falcon, FIPS 204 (ML-DSA) & FIPS 205 (SLH-DSS)

PQ17 Proprietary PRNG for testing encryption algorithms (via RNG software)

AES-256 (ECB,CBC,OFB,CTR)
Enabled by NTC-KEM(McEliece) & FIPS 203 (ML-KEM)

Proprietary key containers with encryption and secure file storage
Use Case Examples for TQ42 Cryptography
Explore how TQ42 Cryptography delivers practical, real-world value through advanced post-quantum encryption.
Elevate your Wi-Fi security with TQ42 Cryptography, by:
- Generating unique, quantum-resistant passwords for each new device connecting to your network
- Encrypting password files using keys derived from the administrator password
- Enhancing security by replacing manual password entry with QR code-based connection in the future
TQ42 Cryptography provides robust digital signature and hashing capabilities, essential for building quantum-resistant blockchain solutions:
- Create secure links between blocks using quantum-resistant digital signatures and hashes
- Ensure the integrity of your blockchain data against potential quantum computing threats
- Implement a quantum-resistant blockchain architecture that safeguards your sensitive information
Achieve Perfect Forward Secrecy (PFS) in your communications with TQ42 Cryptography:
- Generate quantum-resistant keys for each node, contributing to a robust shared session key
- Prevent outside parties from learning the session key by breaking long-term keys
- Establish secure information sharing between users by leveraging quantum-resistant keys in your PFS implementation
Protect your smart home automation system with the power of post-quantum cryptography:
- Secure encryption between mobile devices, IoT sensors, and the cloud-based backend, preserving data privacy
- Ensure the integrity and confidentiality of data transmitted throughout your IoT ecosystem
- Strengthen overall security with authenticated communication channels and system components
Achieve Ultimate Security
Our solutions combine the best of QKD, true randomness (via QRNG), and post-quantum cryptography to secure communication between devices and systems.
Terra Quantum Secure Network
Our patented Quantum Key Distribution (QKD) protocols set the world record for securing long-distance communications with quantum encryption in 2023 and offers security for data in motion. The Terra Quantum Secure Network enables parties to encrypt communications by securely sharing secret keys at high speeds and over long distances.
Entropy as a Service
Contact us to learn more about our single-photon Quantum Random Number Generator (QRNG), designed and implemented according to the latest NIST standard (SP 800-90B) and certified by METAS – available off the shelf and via a SaaS product coming soon.
Key Management System
Leverage Terra Quantum's proprietary key containers with encryption and secure file storage, ensuring the highest level of security for your cryptographic keys.
"Terra Quantum has consistently proven its leading role in driving the second quantum revolution. Its pioneering quantum applications have tremendous potential, for example to solve the imminent quantum cryptography challenges."
-Stephen Nundy, Lakestar
TQSN Differentiators
In the face of evolving quantum threats, Terra Quantum's Secure Network (TQSN) offers a pioneering approach to protecting your critical data in motion. By leveraging end-to-end physical line loss control and optical amplification, TQSN delivers unparalleled security, seamless integration, and global scalability—all while achieving record-breaking data transmission speeds.
Unparalleled Security
TQSN's patented QKD protocol ensures unconditional security without trusted nodes, thanks to its advanced end-to-end physical line loss control capabilities. With a leakage detection precision of 0.001%, TQSN offers zero-trust security for your most sensitive communications.
Seamless Integration
Designed to work with existing infrastructure, TQSN leverages standard optical dark fiber networks, eliminating the need for costly upgrades. This compatibility enables seamless adoption, allowing you to fortify your data security without disrupting your operations.
Global Scalability
TQSN harnesses the power of optical amplifiers to securely transfer keys across distances up to 40,000 km—a feat unmatched by any other QKD solution. As the world's first globally scalable QKD network, TQSN empowers your organization to protect its data across vast distances.
Unrivaled Performance
By leveraging signal repetition through optical amplification, TQSN achieves ultrafast data transmission rates, surpassing other QKD solutions. Leverage the benefits of quantum-secure communication without compromising on performance.
FAQs For Key Takeaways
Demystifying quantum cryptography and its real-world impact.
Quantum security encompasses principles and practices to protect data and communication against threats from quantum computing, which could compromise current cryptographic algorithms. Quantum cryptography uses quantum mechanics principles, like superposition and entanglement, to encrypt and decrypt data, offering potentially unbreakable security.
Quantum cryptography ensures secure communication between two parties, often called Alice and Bob, using Quantum Key Distribution (QKD). QKD allows them to generate a shared, random secret key for encrypting and decrypting messages. A key principle is that any measurement of a quantum system alters its state, so if an eavesdropper (Eve) tries to intercept the communication, her presence will be detected by the changes in the system’s state. This fundamental property of quantum mechanics ensures the security of QKD.
Current cybersecurity relies heavily on asymmetric cryptography for authentication and key exchange. Quantum computers threaten these methods because they can potentially break algorithms like RSA and Elliptic Curve Cryptography. Quantum algorithms, such as Shor’s algorithm, can factorize large numbers much faster than classical algorithms, risking the security of digital communications.
TQSN (Terra Quantum's patented protocol) is quantum-safe because it resists attacks from quantum computers and relies on fundamental laws of quantum physics. It does not depend on computational assumptions, making it immune to higher computational powers. The protocol challenges eavesdroppers to distinguish between non-orthogonal quantum states, which is impossible without errors due to quantum laws. The security is quantified using the Holevo theorem and is theoretically proven based on the second law of thermodynamics and precise loss control. Unlike other protocols, such as BB84, the TQ protocol ensures everlasting security even against future technologies or attacks.
Current challenges of quantum cryptography include high initial costs, complex technical requirements, maintaining quantum states over distances, and ensuring stable environmental conditions. However, the future is promising with ongoing advancements such as transitioning from dark fiber to lit fiber networks, which reduces costs and expands reach by using existing telecommunications infrastructure for Quantum Key Distribution (QKD). Additionally, progress is being made towards dynamic point-to-multipoint configurations, enhancing network coverage and allowing more users to connect securely.