- Quantum computers pose a significant threat to current encryption methods, necessitating new cryptographic solutions for protecting sensitive data in the future.
- Post-Quantum Cryptography (PQC) offers a suite of advanced algorithms designed to secure data against attacks from both classical and quantum computers. These methods can be implemented on existing hardware, providing a practical path to quantum-resistant security.
- Organizations across all sectors need to start preparing for the quantum threat now. By understanding the risks and initiating the transition to PQC, businesses can ensure long-term data security, maintain compliance with evolving regulations, and safeguard against future "store now, decrypt later" attacks.
Post-Quantum Cryptography: The Basics
Quantum computers have fundamental differences to all other forms of technology and their transformative potential poses a significant threat to current cybersecurity measures. If the previous sentence was new information for you, then you are the intended audience for this blog post. If you are already aware and are interested in diving deeper into the details, stay tuned for our subsequent posts.
Quantum Computers and Their Threats
Quantum computers are physical devices that aim to leverage the principles of quantum mechanics in their internal operations. This enables them to complete certain, specific computational tasks, including attacking some extremely common forms of encryption, with unprecedented speed and efficiency. Quantum computers are not yet at the point where they can break the encryption that underpins the world’s internet traffic, but their capabilities are rapidly growing.
There is a clear and obvious need to prepare and implement new cryptographic methods before this threat materializes. This is the point where quantum computers become “cryptographically relevant.” The logic behind the terminology is that post-quantum cryptography consists of security protocols that will still be secure after this happens.
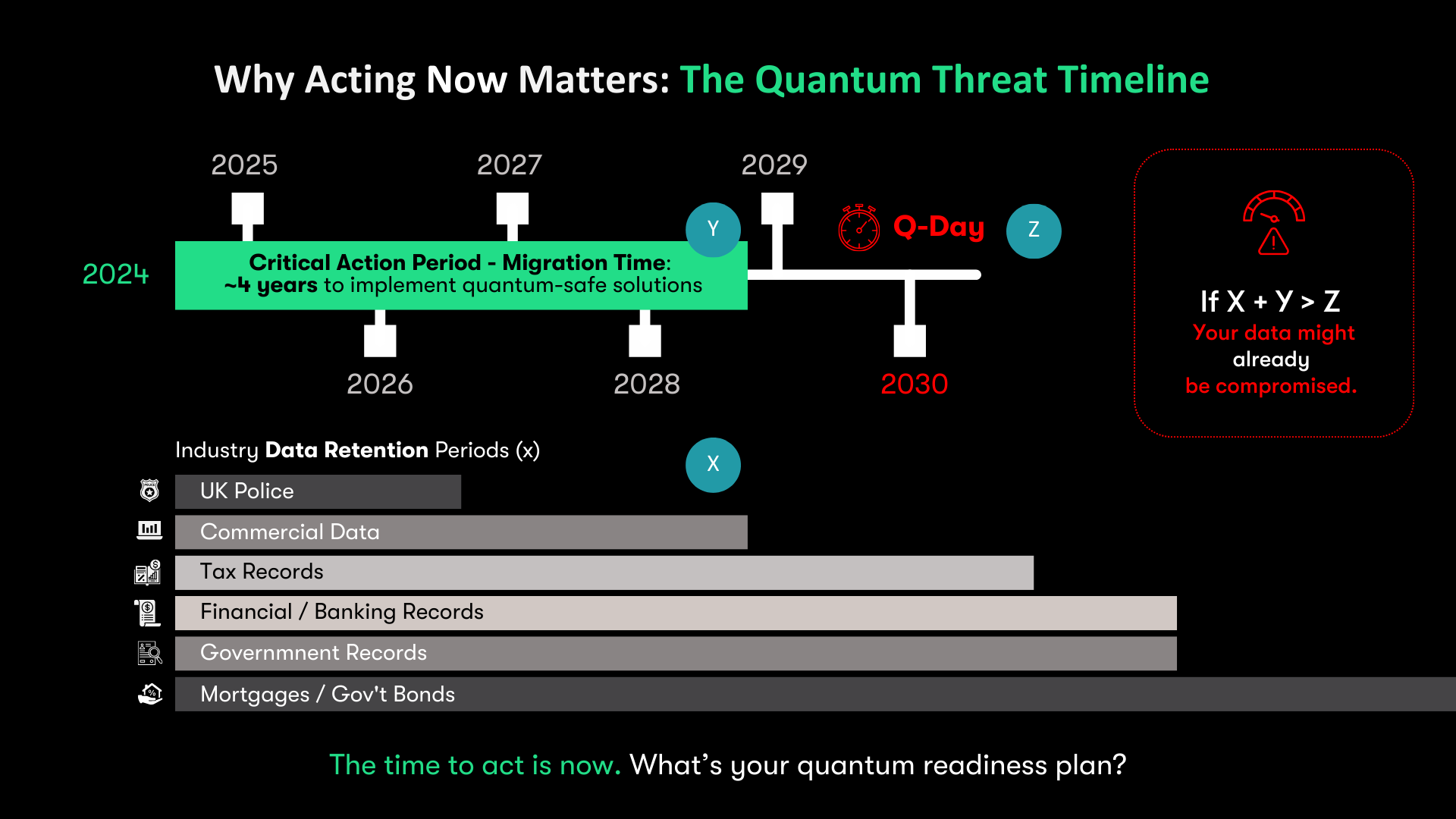
Timeline of the Quantum Threat
While it's challenging to predict exactly when quantum computers will become cryptographically relevant, experts estimate this could happen within the next 5-15 years. However, the threat may already be present for some organizations, as explained by Mosca's Inequality.
Mosca's Inequality states that if the sum of the time it takes to migrate to quantum-safe systems (X) and the required security lifetime of the data (Y) is greater than the time until quantum computers can break current cryptography (Z), then organizations should act now. Mathematically, if X + Y > Z, immediate action is necessary.
This inequality underscores that depending on your industry and the shelf life of your data, you may already be at risk. For instance, sectors dealing with long-term sensitive data, such as healthcare or government, may need to act sooner than others. The "store now, decrypt later" threat further emphasizes the urgency for organizations to start implementing quantum-resistant security measures proactively.
Post-Quantum Cryptography in Context
Post-Quantum Cryptography (or PQC for short) consists of cryptographic algorithms designed to keep data secure even if they are attacked by a fully-fledged, cryptographically relevant quantum computer. PQC is similar to other encryption methods because they can be run on existing hardware. In other words, you do not need a quantum computer to be secure against a quantum computer.
PQC is unlike traditional cryptography in that it has been designed with the capabilities of quantum computers in mind. Once data has been encrypted with PQC, it cannot be decrypted by any of the forms of computation at which quantum computers excel. This makes it a crucial component of future-proof cybersecurity strategies.
NIST’s Role in Standardizing PQC
The Nation Institute of Standards and Technology (NIST) plays a pivotal role in the development and standardization of PQC. NIST has been actively evaluating and standardizing new cryptographic algorithms that can withstand quantum attacks. This process involves collaboration with industry experts to ensure that the new standards are robust and widely applicable. NIST’s efforts are essential for creating a secure cryptographic framework that organizations can adopt to protect their data against quantum threats.
Global Government Recognition of the Quantum Threat
The urgency of preparing for post-quantum cryptography is not just recognized by the private sector but also at the highest levels of government worldwide.
In the United States, The White House issued National Security Memorandum (NSM-10) in May 2022, emphasizing the need to mitigate risks to vulnerable cryptographic systems. NSM-10 set an ambitious goal to mitigate as much quantum risk as feasible by 2035, outlining specific actions for federal agencies and recognizing that this transition extends beyond government concerns. This action underscores the critical importance of quantum-resilient cryptography for national security and economic competitiveness globally.
Since then, the government has been actively driving efforts to ensure the nation's readiness for the post-quantum era, alongside NIST. The White House's involvement in advancing post-quantum cryptographic standards underscores the critical importance of this technology for national security and economic competitiveness globally. It's a clear signal that post-quantum cryptography is not just a concern for tech companies or cybersecurity professionals, but a national and international priority.

Governments around the world are taking similar steps. The European Union Agency for Cybersecurity (ENISA) laid the groundwork with a comprehensive report on post-quantum cryptography in 2021. Building on this foundation, in April 2024, the European Commission released a Recommendation on Post-Quantum Cryptography, encouraging a harmonized approach to the post-quantum cryptography transition, emphasizing the need for coordinated action across member states. The Netherlands has developed a detailed PQC Migration Roadmap, offering organizations a step-by-step transition approach.
In July 2024, the U.S. Cybersecurity and Infrastructure Security Agency (CISA), in July 2024, announced their Post-Quantum Cryptography Initiative to unify efforts with interagency and industry partners. Previously, the NSA's Commercial National Security Algorithm Suite 2.0 provided a timeline for transitioning to quantum-resistant algorithms, mandating PQC use for software and firmware signing by 2025.
The quantum security movement extends beyond Western nations, as demonstrated by the inaugural South-East Asia Post-Quantum Cryptography Summit (SEA-PQC) in 2024 and ETSI’s (The European Telecommunications Standards Institute) Quantum Safe Cryptography Conference held in Singapore this year.
These actions by governments around the world underscore the immediacy of the quantum threat and the need for organizations across all sectors to begin their transition to post-quantum cryptography now. The fact that this is being driven from the highest levels of government adds significant weight to the urgency of addressing this challenge.
Why Organizations Need to Prepare Now
- Data Security and Compliance: Organizations are required by regulations, such as GDPR, to secure their data. A breach due to quantum vulnerabilities could have severe financial, reputational, and legal consequences.
- Futureproofing: By preparing now, organizations can ensure their data remains secure even as quantum computing capabilities advance. This involves understanding potential risks, updating cryptographic techniques, and planning for the transition to PQC.
- Proactive Risk Management: Incorporating quantum risk planning into long-term cybersecurity strategies is essential. This includes conducting risk assessments, engaging with vendors for PQC solutions and educating stakeholders about the quantum threat.
- Avoiding “Store Now, Decrypt Later” Attacks: Cybercriminals might already be collecting encrypted data with the intention of decrypting it when quantum computers advance to the point of being cryptographically relevant. Organizations need to secure their data now to prevent future breaches.
- PQC consists of a diverse set of safe, resilient, and flexible algorithms that benefit from many of the practical lessons that have been learnt by the cryptographic community in recent decades. Adopting PQC is therefore a positive step that improves and modernizes an organization’s cybersecurity practices.
In conclusion, the time to adopt PQC is now. By understanding the risks and preparing for the transition to PQC, organizations can safeguard their data and maintain trust in their digital communications.
Take the Next Step
Whether you are a developer exploring open-source options or an enterprise seeking a commercial-grade solution, TQ42 Cryptography offers a secure path forward in the quantum era. Ready to quantum-proof your systems with a validated, future-ready solution? Contact our team and start planning your roadmap to PQC migration.
Stay tuned for our next blog post in the series, where we'll dive deeper into NIST's PQC Standards and their impact on various industries. We'll explore FIPS 203, 204, and 205, explaining their significance, compliance implications, and effective dates - essential knowledge for navigating your organization's path to a quantum-safe future.